Network admintrators and Service providers are required to be very careful when redistributing Routes between 2 or more routing protocols. The challenges can be faced on redistribution among any of the Routing protocols whether RIP, OSPF, EIGRP or even BGP.
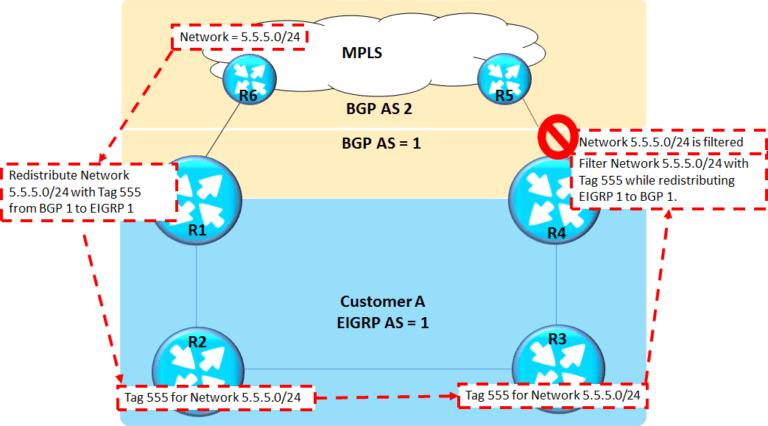
Above shown is one such scenario where TAGs will help filter the routes and mitigating the loops from happening. Customer A has 2 Links from same Service provider as below –
Network 5.5.5.0/24 is advertised by Service provider from 2 entry-exit points
- From R6-R1 Link
- From R5-R4 Link
R1 injects the TAG 555 to while redistributing BGP network 5.5.5.0/24 into EIGRP 1 domain using the route-map tag555 as below
R1 Configuration –
Route-map tag555 permit 10
Match ip address net5
Set tag 555
Route-map tag555 permit 20
Router eigrp 1
Redistribute bgp 1 metric 1000 10 255 100 1500 route-map tag555
The same TAG of 555 is propagated into EIGRP domain and can be dropped while redistributing EIGRP to BGP on R4 which will stop the network Loop from happening.
R4 Configuration –
Route-map tag555 deny 10
Match tag 555
Route-map tag555 permit 20
Router bgp 3
Redistribute eigrp 1 metric 1000 route-map tag555
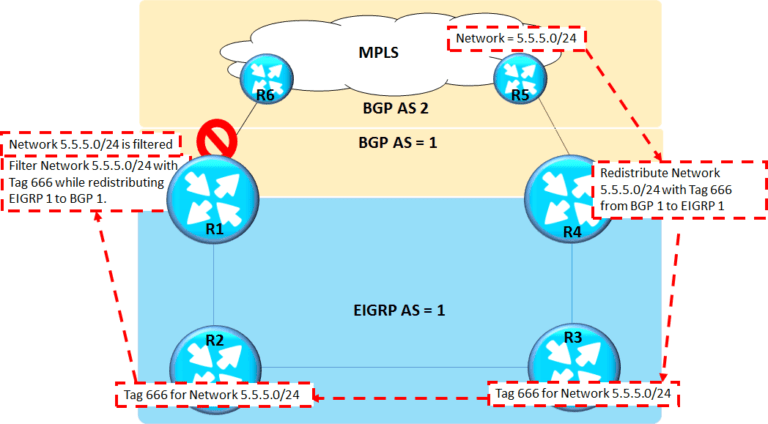
The same tag based blocking needs to be implemented for Network (5.5.5.0/24) learned by R4 via its eBGP neighbor R5.Below is the approach to be followed –
R4 Configuration –
Route-map tag666 permit 10
Match ip address net5
Set tag 666
Route-map tag666 permit 20
Router eigrp 1
Redistribute bgp 1 metric 1000 10 255 100 1500 route-map tag666
R1 Configuration –
Route-map tag666 deny 10
Match tag 666
Route-map tag666 permit 20
Router bgp 3
Redistribute eigrp 1 metric 1000 route-map tag666
Now to check whether the tag555 and tag666 have been implemented and able to block Network 5.5.5.0/24, we issue the following commands on
R4 Configuration –
Show ip bgp neighbor 192.168.45.5 advertised-routes
(The above command is issued to verify that R4 is not advertising network 5.5.5.0/24 to R5. R4 denies routes with tag 555 advertised to R5 using Route Map)
R4#sh ip bgp neighbor 192.168.45.5 advertised-routes
Network Next Hop Metric LocPrf Weight Path
*> 2.2.2.0/24 192.168.34.3 1000 32768 ?
*> 3.3.3.0/24 192.168.34.3 1000 32768 ?
*> 192.168.12.0 192.168.34.3 1000 32768 ?
*> 192.168.23.0 192.168.34.3 1000 32768 ?
*> 192.168.34.0 0.0.0.0 0 32768 ?
*> 192.168.45.0 0.0.0.0 0 32768 i
Total number of prefixes 6
R1 Configuration –
Show ip bgp neighbor 192.168.15.5 advertised-routes
(The above command is issued to verify that R1 is not advertising network 5.5.5.0/24 to R6. R1 denies routes with tag 666 advertised to R6 using Route Map)
R1#show ip bgp neighbor 192.168.16.6 advertised-routes
Network Next Hop Metric LocPrf Weight Path
*> 2.2.2.0/24 192.168.12.2 1000 32768 ?
*> 3.3.3.0/24 192.168.12.2 1000 32768 ?
*> 192.168.12.0 0.0.0.0 0 32768 ?
*> 192.168.15.0 0.0.0.0 0 32768 i
*> 192.168.23.0 192.168.12.2 1000 32768 ?
*> 192.168.34.0 192.168.12.2 1000 32768 ?
*> 192.168.45.0 192.168.12.2 1000 32768 ?
ABOUT THE AUTHOR

I am here to share my knowledge and experience in the field of networking with the goal being – “The more you share, the more you learn.”
I am a biotechnologist by qualification and a Network Enthusiast by interest. I developed interest in networking being in the company of a passionate Network Professional, my husband.
I am a strong believer of the fact that “learning is a constant process of discovering yourself.”
– Rashmi Bhardwaj (Author/Editor)